In the news
Digital Superbugs
The recent NotPetya and WannaCry ransomware incidents have highlighted the vulnerability of healthcare systems to untargeted cyber attacks. Chris Lo considers what makes healthcare organisations so susceptible to these digital superbugs, and what steps can be taken to reduce the risks facing this vital sector
You don’t have to look much further than the headline news to observe the growing threat that cyber attacks pose to individual users, businesses and essential services. The latest large-scale breach to hit the front pages – at the time of writing, at least – is the so-called NotPetya ransomware attack, which first struck in Ukraine before spreading to thousands of users around the world. Organisations stricken by the attack included pharmaceutical giant Merck and Pennsylvania’s Heritage Valley Health System, the latter of which was forced to postpone surgeries and shut down offices, labs and diagnostic services.
It’s the kind of crisis for which the UK’s National Health Service should have considerable sympathy, having been the most high-profile victim of WannaCry, another widespread ransomware attack that took place in May.
Within hours of first contact, the attack caused chaos at hospitals and health centres up and down the country as computer systems at more than 40 NHS trusts were shut down in response to the incident, sending patients home without care and leaving some staff reliant on pen-and-paper systems and their own mobile phones to run even skeleton services. Just a few weeks later, the shared drives of University College London were hit by another ransomware incident, causing a number of associated hospital trusts to pre-emptively suspend their e-mail servers.
“This isn’t going to go away,” says Tony Proctor, a veteran cybersecurity specialist and principal lecturer at the University of Wolverhampton. “In general, criminals don't rob banks anymore, they do it online – it’s much easier if you know how. If we think about the threats to health services, I think unfortunately, there you’ve got it all. The NHS, as an information environment, is tremendously complex.”
The cyber threats of the modern era have left healthcare organisations more vulnerable than ever to attacks that impede their fundamental ability to save lives and improve public health. But what makes healthcare networks so exposed to cyber attacks, and what steps can be taken to reduce the risks facing this vital sector?
Ghosts in the healthcare machine
The NHS may have been the biggest health system to suffer a large-scale hack in recent memory, but the common ground shared between healthcare organisations makes these sorts of attacks an international, cross-sector problem. Strained IT budgets, small security teams and the sheer size and complexity of clinical networks leaves healthcare systems susceptible to a broad range of attack types and vectors, while the life-saving and often time-critical nature of their work means the stakes could not be higher.
Cyber attacks pose a threat to virtually any industry, but the healthcare sector works under conditions that make it particularly vulnerable to even the broadest untargeted malware. Hospitals, clinics and doctor’s surgeries tend to operate on large, decentralised IT networks and make use of connected medical devices that are often hugely difficult to upgrade and patch against modern cyber threats.
Regularly applying the latest patches to counteract newly-identified exploits is a core component of any enterprise’s cybersecurity strategy, but the intense regulation of hospital computers and medical devices – not to mention the need for near-constant availability and connectivity of these devices – makes a meal out of even basic patching protocols.
“Most of this is non-targeted or automated malware, and the NHS, because of the nature of its systems, magnifies the risk of those attacks succeeding.”
“Attackers aren’t necessarily saying ‘we will target the NHS’,” says Gabe Chomic, UK chapter president of the Information Systems Security Association. “Most of this is non-targeted or automated malware that goes out there and follows a variety of different attack vectors, and the NHS, because of the nature of its systems, magnifies the risk of those attacks succeeding.
“It’s widely said that the majority of embedded medical systems that would use an operating system – which could be £1m-£2m systems, MRI machines and so on – are running out-of-date legacy software that cannot be upgraded and remains vulnerable. It’s one thing to upgrade a computer; it’s another thing to upgrade a multi-million pound MRI machine, and you don’t want to take it out. So that challenge just continues to magnify the potential impact of an attack.”
Given that the majority of attacks affecting healthcare organisations are untargeted or automated in nature, and hit healthcare systems collaterally, the focus should be on the healthcare network vulnerabilities that leave facilities open to the broad threats that zip around in digital space every day. Even so, limited budgets, combined with the size and complexity of the clinical environment, paint a bewildering picture for healthcare decision-makers who are primarily focused on clinical outcomes rather than IT security.
“Sad to say, I work in a profession where, historically, we’ve had a lot of people who are very keen to cry wolf whenever they can,” says Chomic. “So you have a situation where security’s hard to manage and measure; the number of services that you deliver is easy to measure and you have us cybersecurity professionals in the corner saying everything is going to break every year. And you end up with a risk model, and a risk decision, that is very difficult to assess or justify after the fact.”
Key Facts
Only 0.07% of WannaCry victims paid the ransom
Source: Barkly
Holding essential data to ransom
Despite examples of prominent ransomware attacks existing since 2005 and rapidly increasing in frequency since around 2012, very few NHS workers would have heard the term before their rude awakening with the WannaCry attack earlier this year. Ransomware attacks don’t seek to delete or steal data; instead, these malicious payloads encrypt important files, denying access until a ransom is paid.
Today’s connected world has accelerated the iterative process of this malicious software, and WannaCry, which is now up to its sixth or seventh iteration, is a perfect example. The risk of ‘zero-day’ attacks – those that have not been encountered in the wild before – is higher than ever.
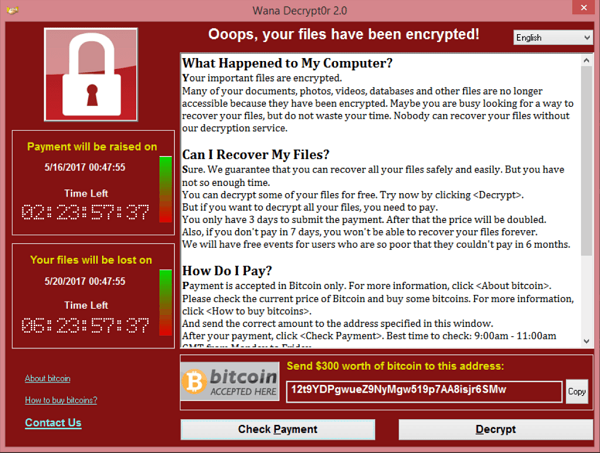
The now infamous alert box that informed users that their files had been encrypted by WannaCry
“[WannaCry] was using two exploits that were leaked from America, from the NSA’s database of sneaky tricks,” says IBM Security associate partner Gavin Kenny.
“A few weeks after WannaCry, actually there was a far more potent ransomware released into the wild that had six of those exploits built into it. So the threat is constantly evolving, in very sophisticated ways and at an incredibly rapid pace.”
“The threat is constantly evolving, in very sophisticated ways and at an incredibly rapid pace.”
With ransomware particularly rife, what can healthcare organisations do to minimise the risk of a major incident? One option, and one that has been used by healthcare systems, is simply to pay the ransom, but while attackers are likely to decrypt files upon receiving the payment because, as Proctor puts it, “these guys are running a business model”, there are no guarantees.
In any case, paying malicious attackers to regain access to your own systems is hardly an acceptable solution. The main preventative measure to protect against ransomware schemes is a thorough and comprehensive back-up system so that any encrypted data can be recovered. It might be easier said than done in a healthcare setting, but relatively simple IT security ‘hygiene’ measures – back-ups, patching, firewalls and anti-virus software in combination with a well thought-out response plan – is usually enough to counteract all but the most innovative targeted attacks.
“The crucial thing is making sure that your data is backed up in a separate location – it can’t be encrypted at the same time,” says Kenny. “It’s making sure, as with any emergency planning, that firstly there is an emergency plan and that those plans are exercised, so that hospitals can quickly identify – this involves some form of monitoring – and isolate an infection using security controls that have been built into the systems, and then deploy a proven plan that allows them to eradicate the infection and re-build the lost data from their back-ups. If they can do that, then actually ransomware will cease to be a problem.”
Key Facts

The attackers made a total of $135,500 from the ransomware
Source: Colin Skeith
Making it easy to do the right thing
As online threats continue to grow in sophistication and variety, the cybersecurity industry is looking towards more advanced technologies to gain an edge over their criminal adversaries. In an environment as sensitive as healthcare, it’s also important that cybersecurity doesn’t exist as a niche corner of the system, badgering users and shovelling endless security protocols into their laps while ignoring the core tension between security and useability.
“We need to make it easy to do the right thing,” says Kenny. “Clinicians and medical staff of any trust did not join the medical profession to think about cybersecurity. These are dedicated, intelligent people who do what they do to save lives and to make people’s lives better. We need to make sure that security systems make their day-to-day lives easier.
“Good security should make it easier to log on in the morning. Good security makes it easier to use multiple devices, whether that’s a tablet or your phone, even if you have a locum doctor. We have cases where a locum doctor has come to work somewhere for four weeks, but it takes them six weeks to get a log-on. That’s not helping.”
“Good security should make it easier to log on in the morning.”
Blockchain – the buzzword of the moment in many tech circles – is a technology that could have significant practical applications in the healthcare sector, among many others. The technology is essentially a transparent and highly secure digital ledger used to record transactions (financial or otherwise), grouping them into chronologically-ordered ‘blocks’. The inherent security and transparency of such a system could have particular uses in tracking access to electronic patient records, which have proven less than secure in the past. The EU’s General Data Protection Regulation, which is due to come into force in May next year, will sharpen the already significant concerns over patient data integrity.
“I think the crucial change that blockchain can bring is around patient records,” Kenny says. “Not necessarily around stopping people accessing them, but it will show you exactly who accessed your record, at what time, and what they did with it. It locks in not only the changes and the additions, but also what went before. So you’ll never be able to change something forever, because if you go backwards and forwards in time, you will be able to see, through blockchain technology, where something was changed.”
Key Facts

The patch to protect against WannaCry was available for 59 days prior to the attack
Source: Microsoft
Artificial intelligence: the next frontier
There is a growing chorus of voices in the IT security sector championing artificial intelligence and machine learning as a core component of the most advanced and unobtrusive security systems. Kenny notes that IBM Security has been testing AI-driven digital systems, and assistance from a self-learning programme can reduce the time taken to identify and respond to a cyber attack from hours to minutes.
One successful example is the Enterprise Immune System offered by Darktrace, a UK-based cybersecurity firm founded in 2013 with a combination of Cambridge University machine learning specialists and veterans of UK intelligence agencies. The system, which is driven by unsupervised machine learning, protected a number of Darktrace’s clients – including an unnamed NHS agency – during the WannaCry outbreak.
The Enterprise Immune System takes its inspiration, appropriately enough for the healthcare sector, from the human immune system. Instead of weighting cyber defences at the digital perimeter and looking out for previously-encountered attack patterns, Darktrace’s system instead starts from within a network, learning what ‘normal’ looks like so it can detect anomalies and provide prompt warnings to co-ordinate a response.
“It is critical for us to free up those security teams from managing security tools themselves, and concentrating on finding the threats and making decisions.”
“We have a protective layer of skin that protects us from the outside world; when things get into our body our immune system is then able to understand what is part of us and what is not, and take action,” explains Darktrace director Mariana Pereira. “That is the same as Darktrace’s immune system; it understands the pattern of life of a network, users and devices, and based on that understanding, it works out what is anomalous behaviour and we’re able to take an autonomous response capability.”
Incorporating AI into the system, which has recently been expanded with the launch of Darktrace’s Antigena autonomous response technology (the digital ‘antibodies’ to the company’s wider immune system), helps to offload much of the day-to-day cybersecurity burden away from IT teams, allowing human workers to concentrate on making key decisions.
“We hear about lean IT teams and low budgets [in healthcare], and so for Darktrace it is critical for us to free up those security teams from managing security tools themselves, and concentrating on finding the threats and doing what humans do best, which is making decisions,” Pereira says. “The machine learning and artificial intelligence components of Darktrace really help in what is essentially a cyber arms race.”
Key Facts

As of December 2016, 90% of NHS Trusts were still using Windows XP
Source: Barkly
Incorporating the human element
Cutting-edge digital technologies are certainly helping to stack the odds in favour of security teams, but it would be perilous to consider technology in isolation as a silver bullet that will slay the hacker threat overnight. It’s vital to remember that the cybersecurity eco-system is made up of not just software, but people as well.
The much-discussed ‘insider threat’ in cybersecurity might come from a disgruntled employee with an axe to grind, but could just as easily could come from a single misjudged click on a suspect e-mail. We’re only human after all, and establishing a culture of good cybersecurity practice among healthcare staff, from top to bottom, is a vital means of strengthening the human links in the security chain. Governments can set a policy direction and provide advice and support – along the lines of the UK’s Cyber Essentials scheme – but it’s up to healthcare organisations to ensure that cybersecurity fundamentals are sinking in.
“The technical processes required and the implementation may well fit in the computing department, but cybersecurity is now part of governance,” argues Proctor. “It has to be. The main standard for cybersecurity is ISO 27001, and one of the things that’s very clear in that is that security has to be driven from the top.
“From some of the security officers that I’ve talked to – and it’s perhaps no surprise at a time of constrained budgets – one of the biggest problems they have is getting the decision-makers to agree to spend money on cybersecurity. And then, anecdotally, these people are leaders, are they following best practices for cybersecurity? Because sometimes I’ve seen senior people circumvent security because they want to share their password with their PA. And that’s not good enough.”
“One of the biggest problems security officers have is getting the decision-makers to agree to spend money on cybersecurity.”
Chomic also raises concerns about the yawning skills gap that is forming in the cybersecurity industry. Analysis carried out by information security non-profit (ISC)² estimates that the cybersecurity sector in the UK will be short of 1.8 million professionals by 2022. Fewer IT security professionals looking for work means shortfalls of expertise at a time when healthcare organisations need it most, while also putting public sector employers at a distinct disadvantage in the market.
“It’s created an extraordinarily beneficial job market for security professionals looking for work, and it has therefore equally disadvantaged local government, central government and local authorities, such as NHS authorities, which are constrained by public sector pay scales,” says Chomic.
“We all have our part to play,” adds Proctor. “It’s about government, it’s about education and higher education, it’s about industry helping to provide those opportunities. It’s about industry working with education and telling us what their needs are. Talent is needed across the piece. Cybersecurity matters to every organisation, whether they’re a corner shop or the NHS. That’s the nature of the world now.”
Key Facts

20% of NHS Trusts are thought to have been affected by WannaCry
Source: NHS
Community immunity with data sharing
Data-sharing is an important way for healthcare IT teams to reduce their individual workloads and boost collective knowledge, especially if cybersecurity consultants are in increasingly short supply.
It’s the reason IBM Security has made its X-Force threat intelligence feed freely available online; it’s the reason the British government has established the Cyber Information Sharing Partnership initiative; and it’s the reason Tony Proctor has spent the last decade developing information-sharing networks for the West Midlands region of the UK.
“The threat information is one side, but the other side of it is we’re able to get people together in a closed, safe environment,” says Proctor. “They talk about the incidents that have happened to them and then the others can benefit, because if they have the same problem, they know it’s been dealt with previously.”
“Sharing details of known cybersecurity vulnerabilities and threats across healthcare groups can help build up a ‘herd immunity’ effect.”
In the same way that many deadly diseases have been eradicated with vaccine programmes, sharing details of known cybersecurity vulnerabilities and threats across healthcare groups can help build up a ‘herd immunity’ effect, where useful intelligence gained in one organisation can spread to the rest.
At the sharp end of cybersecurity, healthcare organisations have to rely on people to turn IT security technologies into more than the sum of their parts. In an age when new malware strands are appearing online at an estimated rate of two a day, there’s no doubt that health systems will continue to fall victim to untargeted cyber attacks in the months and years to come. Minimising the risks to essential healthcare services will require a big-picture effort, combining well-informed staff with comprehensive security systems and considered response plans. Artificial intelligence might be the future of cyber defences, but any effective security strategy, at its heart, needs to put people first.
NHS England, NHS Digital and the UK National Cybersecurity Centre were all contacted to contribute to this feature; all declined or did not respond by the time of writing.